Welcome to Day 4 of Airplane Launch Week ✈️
At Airplane, security is at the heart of everything that we do. Our customers rely on Airplane to run their most sensitive operations safely and securely. That’s why we’ve focused on implementing improved security features to make internal tooling safer for all of our customers.
We are proud to announce a suite of new enterprise security features that will help you exceed your most rigorous safety and compliance requirements.
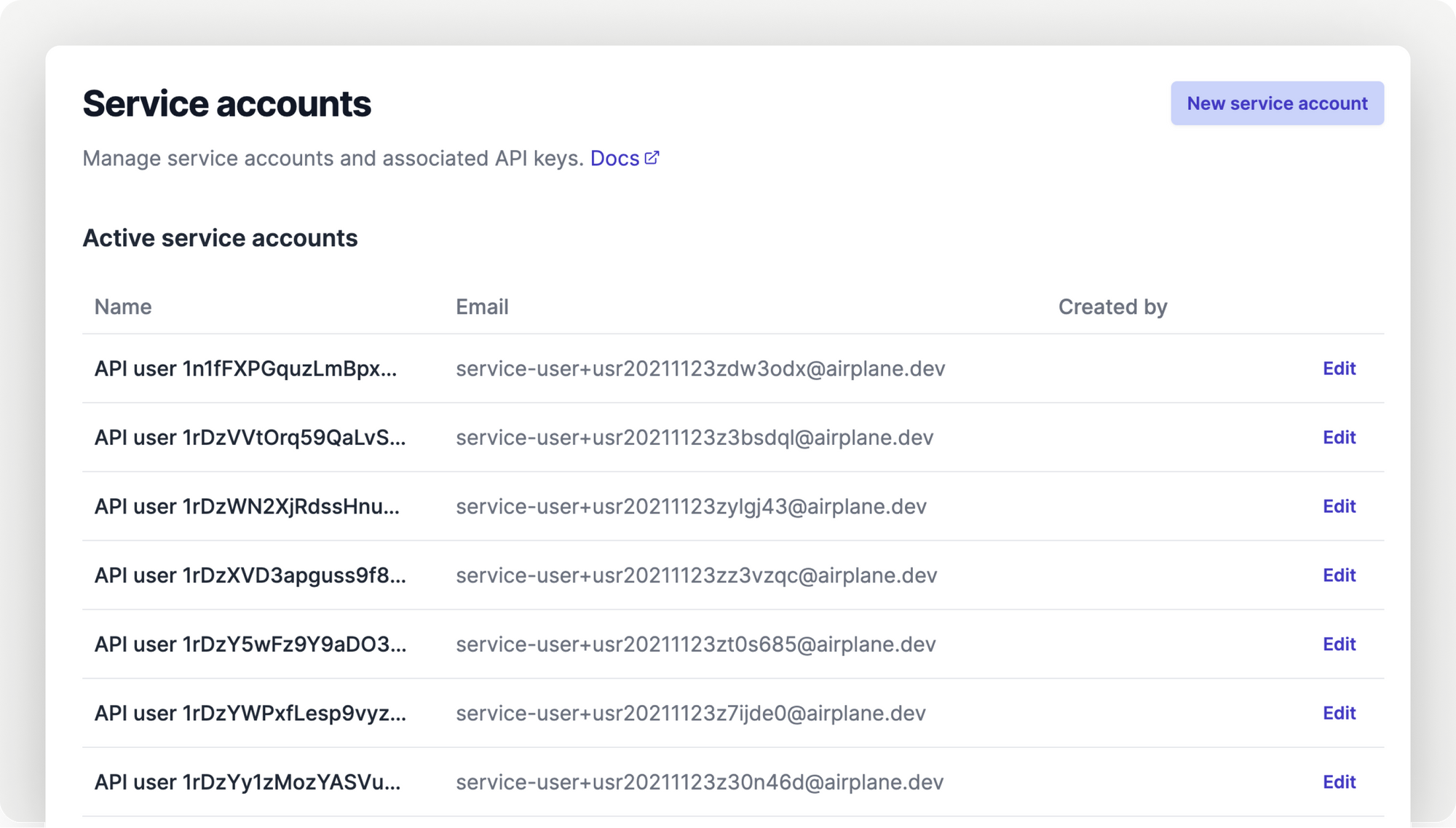
Service accounts
You can now use service accounts in Airplane to easily rotate API keys, assign fine-grained permissions to API users, limit permissions on a per-environment basis, and more. This type of account offers a controlled, efficient way to facilitate automation and secure interactions between applications and services. Service accounts can be assigned permissions that can be used to execute tasks, interact with the Airplane API, and kick off deployments.
Check out the service account docs →
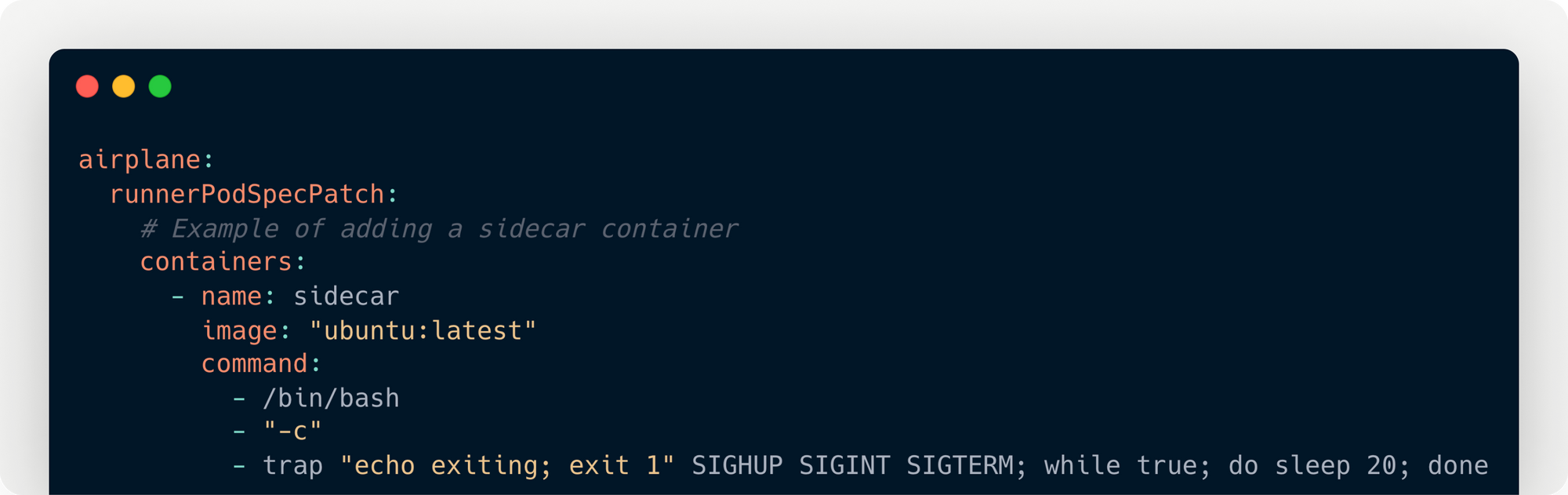
Custom pod patches
Airplane now supports applying arbitrary patches to the agent runner pods’ Kubernetes configurations. This allows fine-grained control over pod configuration for better integration with your particular Kubernetes implementation. In addition, you can mount secret volumes to access API keys and other sensitive data, add sidecars to support monitoring or other additional functionality, define specific networking configuration requirements and more!
Check out the custom pod patches docs →
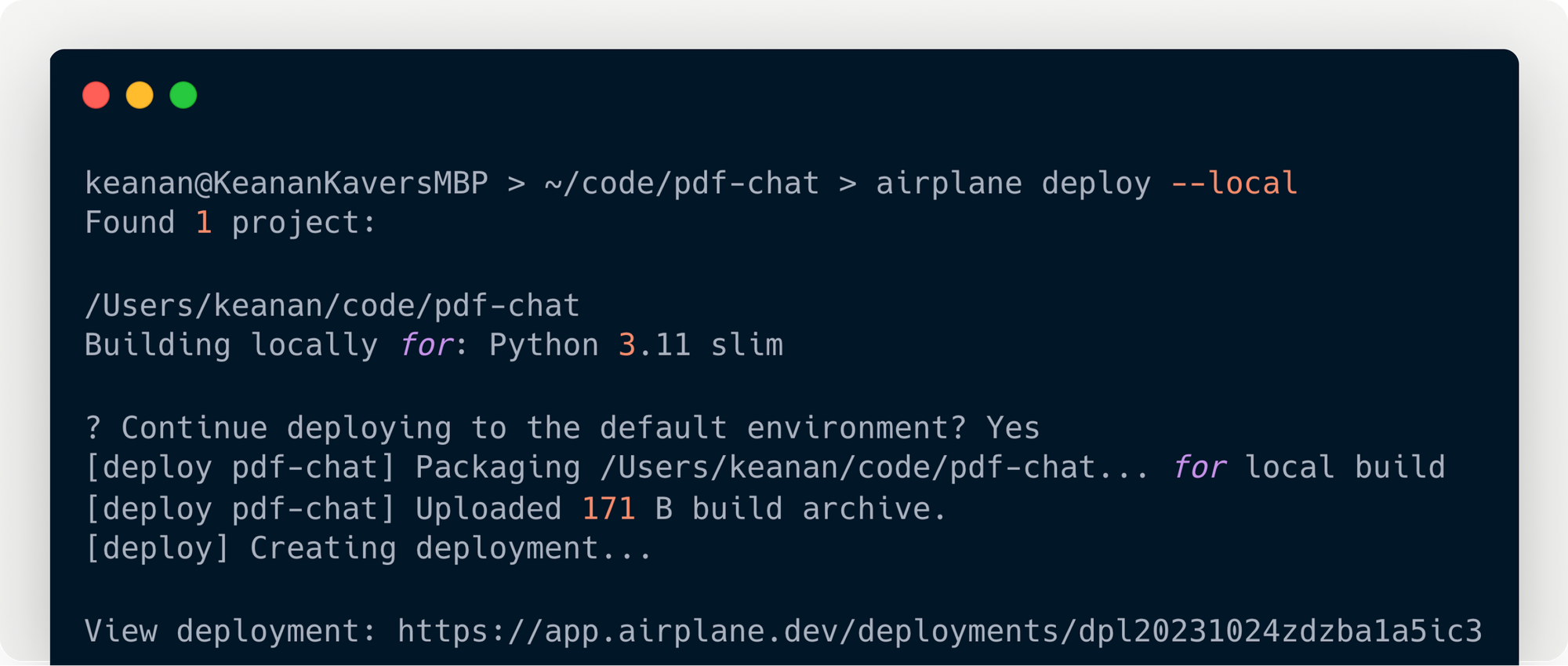
Self-hosted builds
If you want more control and security when it comes to your image builds, you can now modify the default behavior of airplane deploy to run a deployment locally and then push the resulting images to Airplane repositories. This means that you have full control and visibility over the entire build system and that you know exactly what’s being run on your Airplane instance.
Check out the self-hosted builds docs →
Self-hosted task input storage
Self-hosted storage now supports inputs in addition to outputs. Self-hosting your input data (e.g., task run parameters, file uploads, etc.) ensures that it remains in your environment and does not transit through Airplane’s systems, keeping your data safe and secure.
Check out the self-hosted task input storage docs →
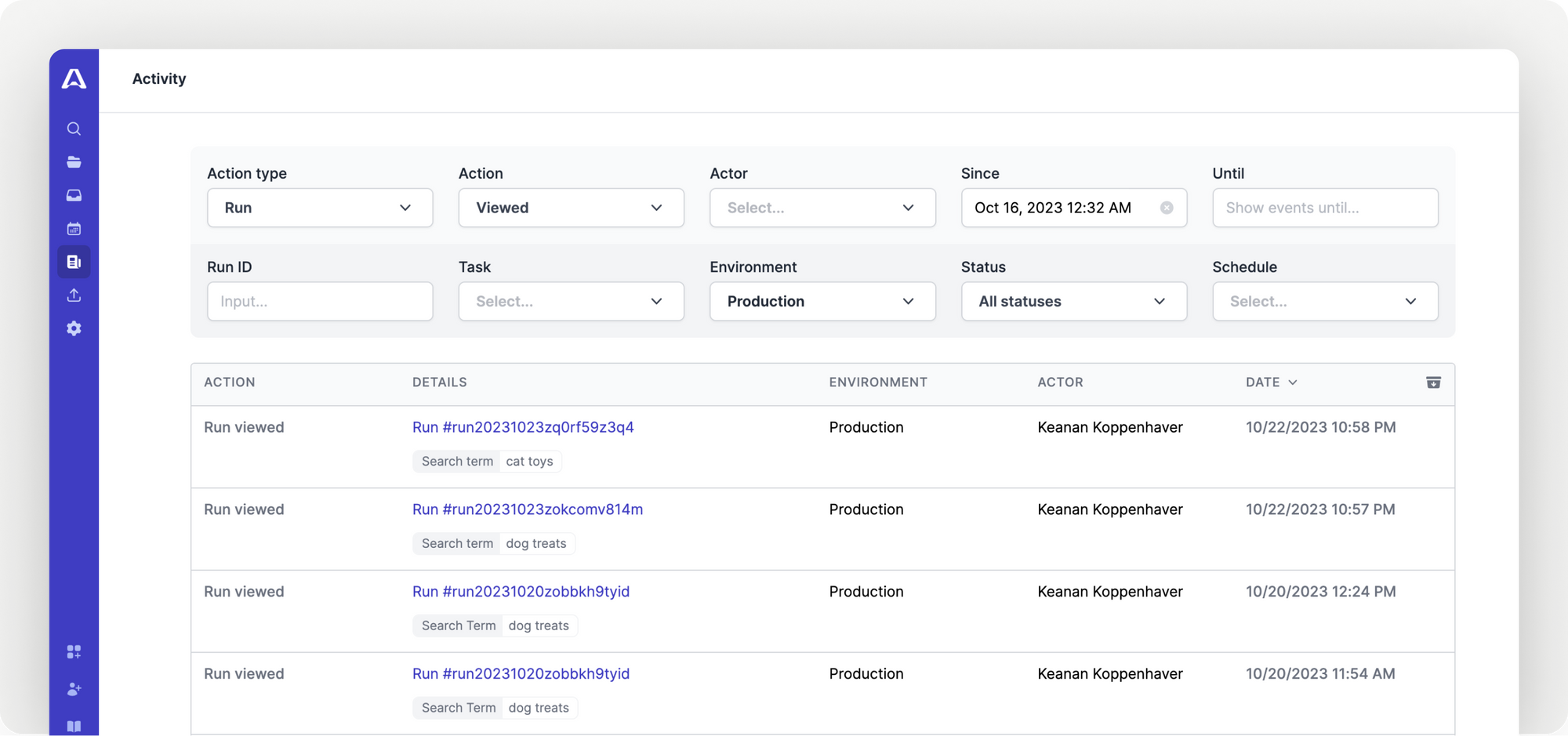
Audit logging improvements
You can now generate audit log entries when runs are viewed. This allows for higher visibility into which runs your teammates are accessing.
Check out the audit log docs →
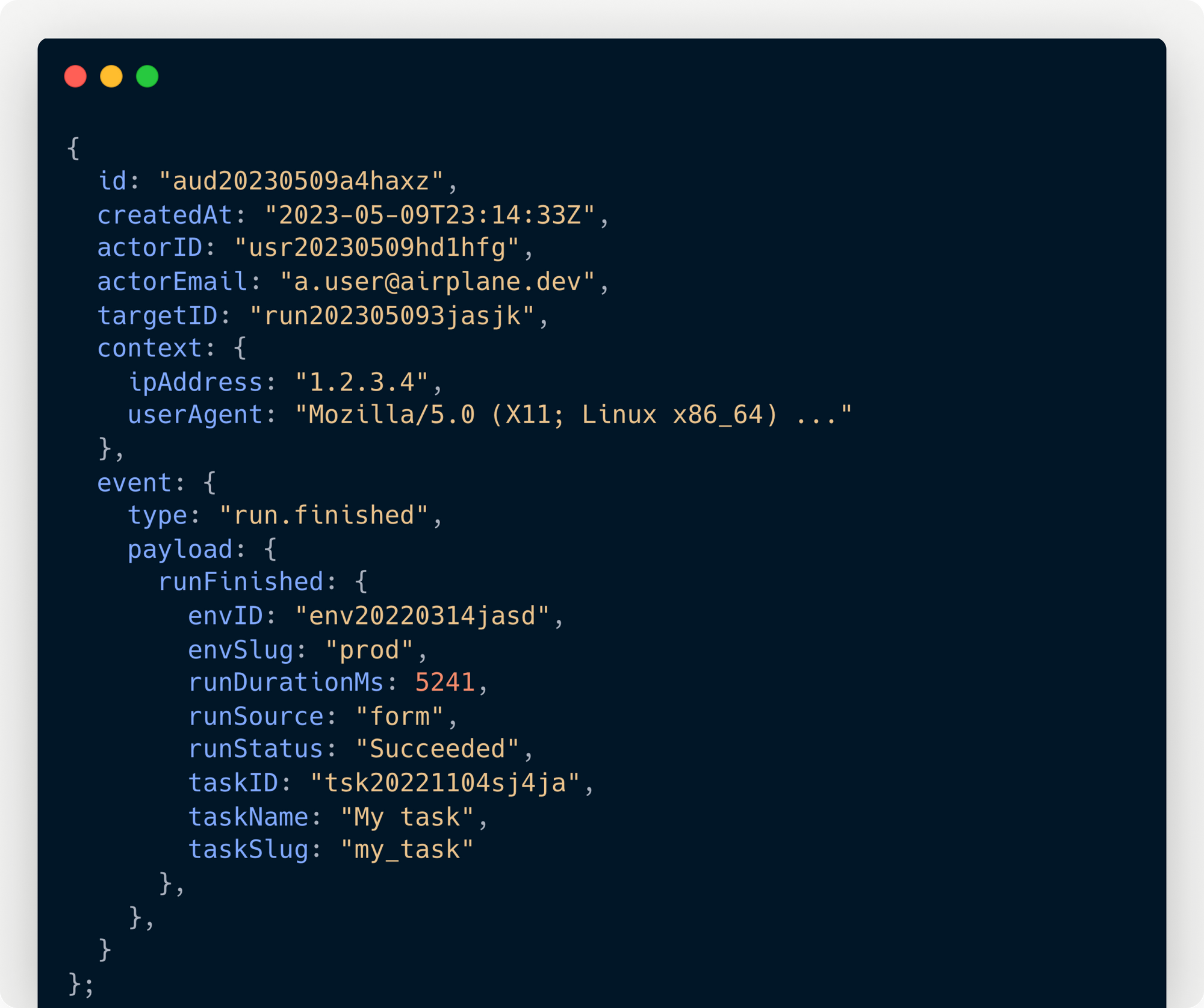
Log drains
You can now stream Airplane audit events to your own observability systems. “Drains” can be configured for Datadog, Open Telemetry, or webhook-based collectors. Once this is done, the Airplane events can be processed and viewed inline with other, non-Airplane-related log events in your observability stack.
Check out the log drain docs →
Try it out
The introduction of service accounts, custom pod patches, improved audit logs, and more are just the start of our continued efforts towards making Airplane your go-to control panel for all of your sensitive operations. To try out our new security features for yourself, sign up for a free account or book a demo and start building safe, efficient internal tools today.