Airplane was built to help companies operate safely and securely. In this post you'll find a list of product features that support security as well as a list of security-focused use cases.
Security and compliance features:
- Approval flows
- Audit logs
- Encryption
- Permissions
- Self-hosted agents
- SOC 2
- SSH tunneling
- SSO and two-factor auth
Security use cases:
- Health checks, monitoring, and reporting
- Access controls on sensitive operations
- Database backups
- Debugging issues
Please read on for more details on each.
Security and compliance features
We've built the following features to keep your data and account secure.
Approval flows
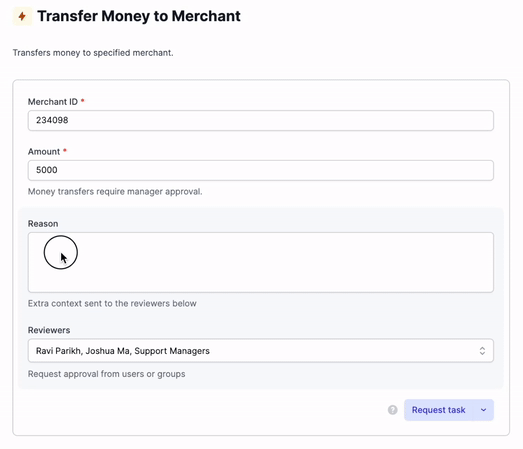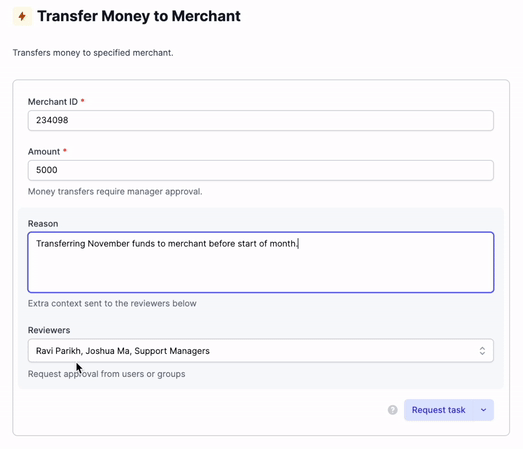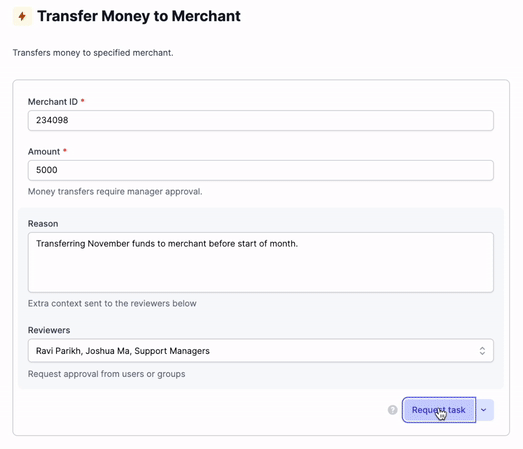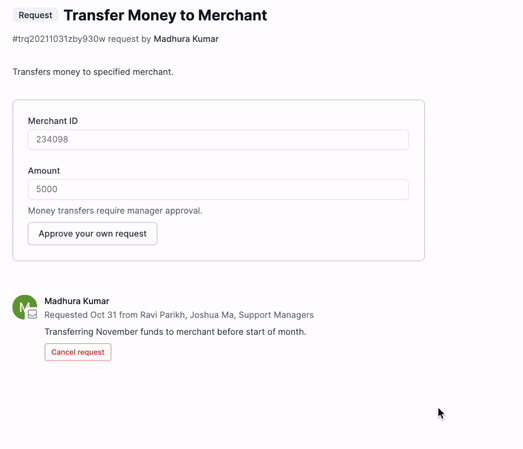
Enforce that certain tasks or runbooks can only be executed after another user has approved them. Configuring an approval flow takes minutes and allows you to limit which individuals or groups are allowed to view, request, execute, and approve tasks and runbooks.
Requests can be sent to individuals or to groups. These requests can also be received and approved directly via Slack or email.
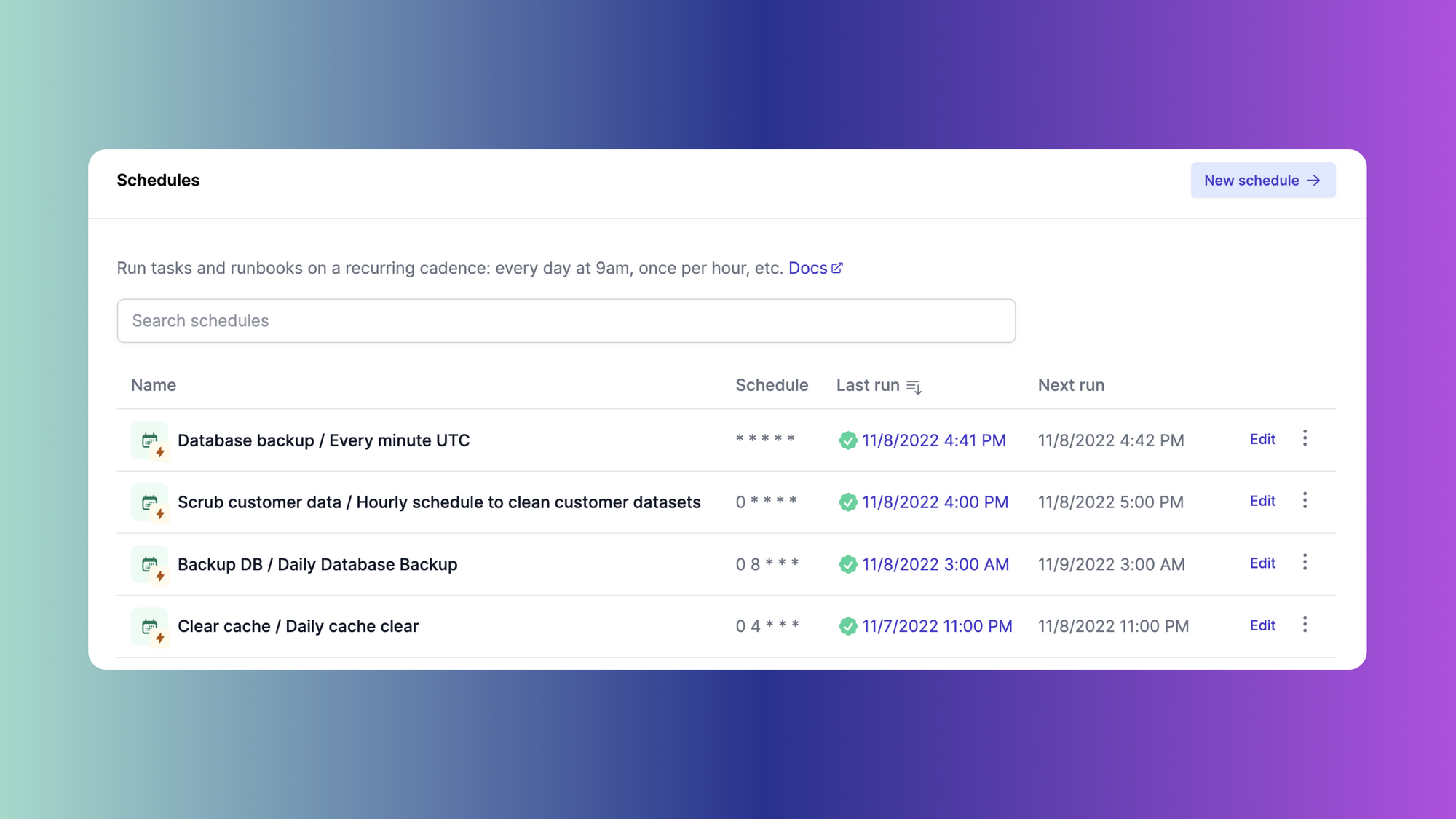
Audit logs
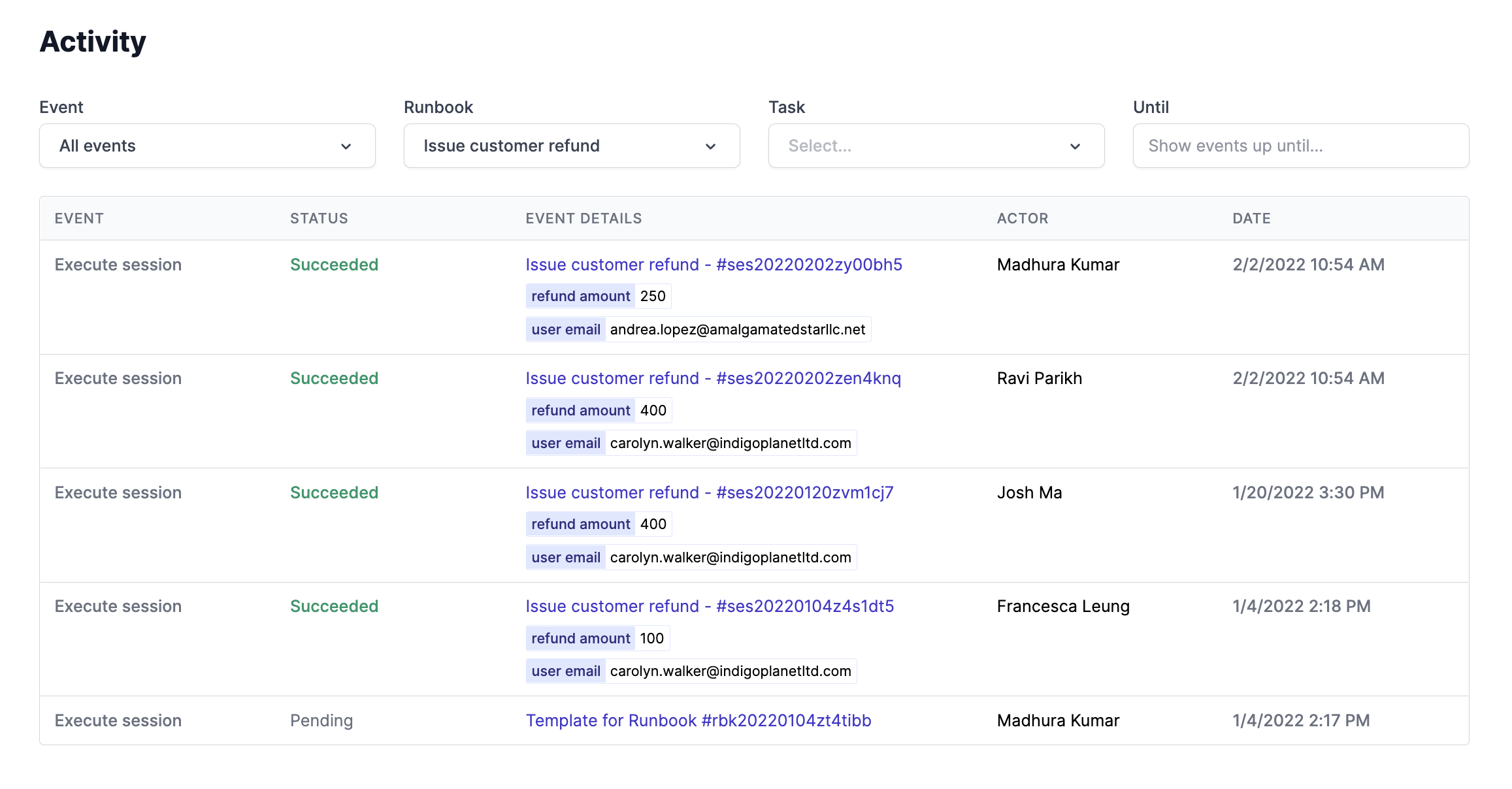
Every task run and runbook session is logged on the Activity page, available from the navigation bar. You can view detailed logs on a run-by-run basis. These logs contain executors, time and date stamps, environments, constraints, timeouts, and more.
Encryption
All data in transit is encrypted over HTTPS/TLS between you and Airplane's servers. All data at rest is stored encrypted and replicated for durability.
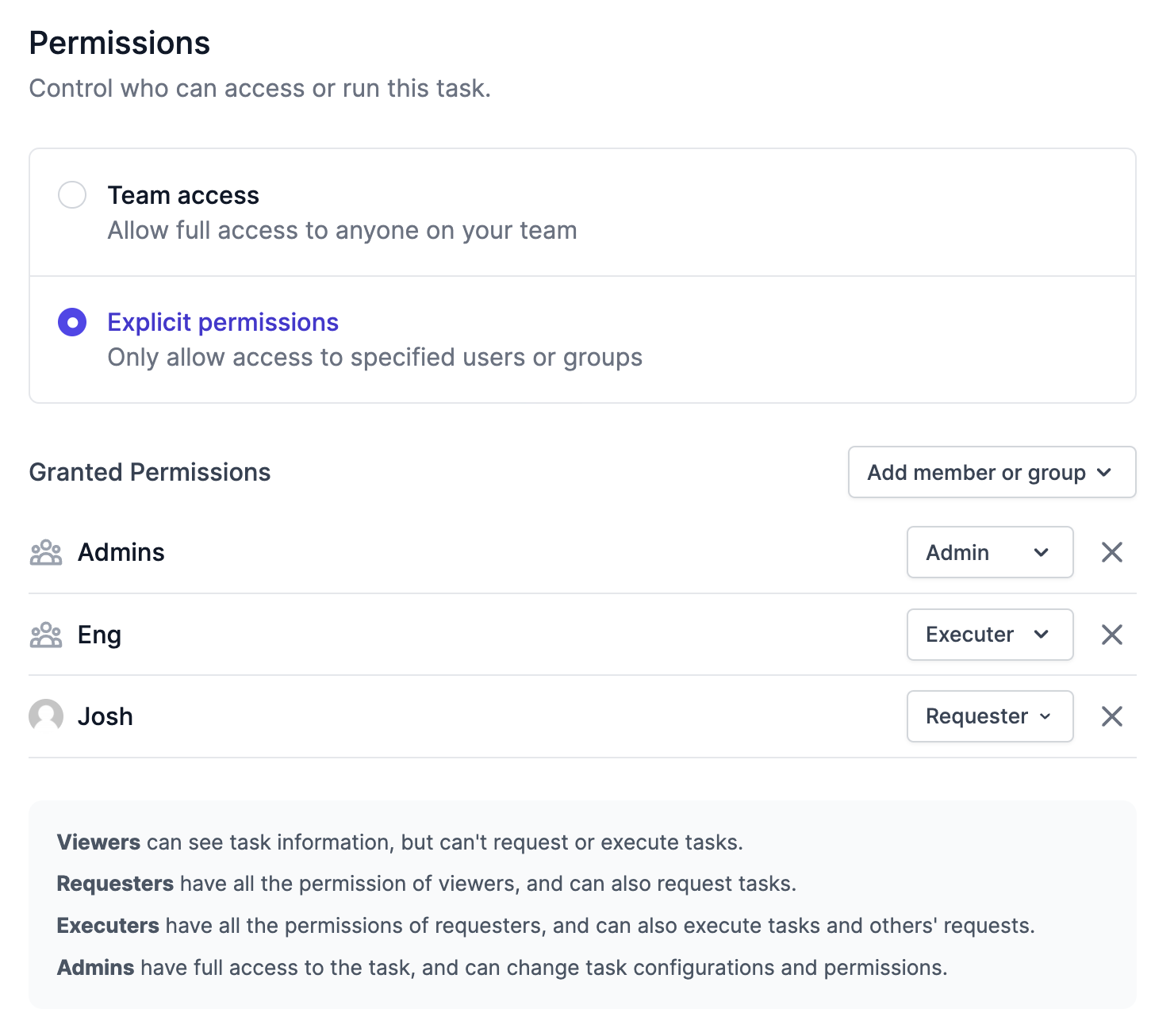
Permissions
Airplane's permissioning system allows for fine-grained, role-based access controls across your organization. Permissions can be assigned directly to users or to groups of users. You can set explicit permissions on individual tasks and runbooks for granular control.
Self-hosted agents
If you'd like execution to happen in your environment, you can self host the agents running scripts and queries in your own infrastructure. Airplane also offers Airplane-hosted agents that are fully managed by Airplane and require no customer management.
SOC 2
Airplane is SOC 2 compliant. This means that we regularly undergo third-party external penetration tests, conduct background checks of new employees, have all employees go through security awareness training, and more. To access our SOC 2 report, please email us at [email protected]. Our team is also happy to fill out a security questionnaire with your OpSec team if necessary.
SSH tunneling
You can use SSH tunneling to connect to a SQL database in your VPC.
SSO and two-factor auth
Airplane currently supports G Suite and SAML SSO, allowing customers to enforce that users sign in using customer-managed identity providers. G Suite SSO is restricted to domain(s), so that customers can ensure users only sign in using customer-managed G Suite accounts.
Two-factor authentication for application login can be enforced at the identity provider level (e.g. by turning it on within G Suite).
Security use cases
Here are how some of our customers are using Airplane to run internal operations safely:
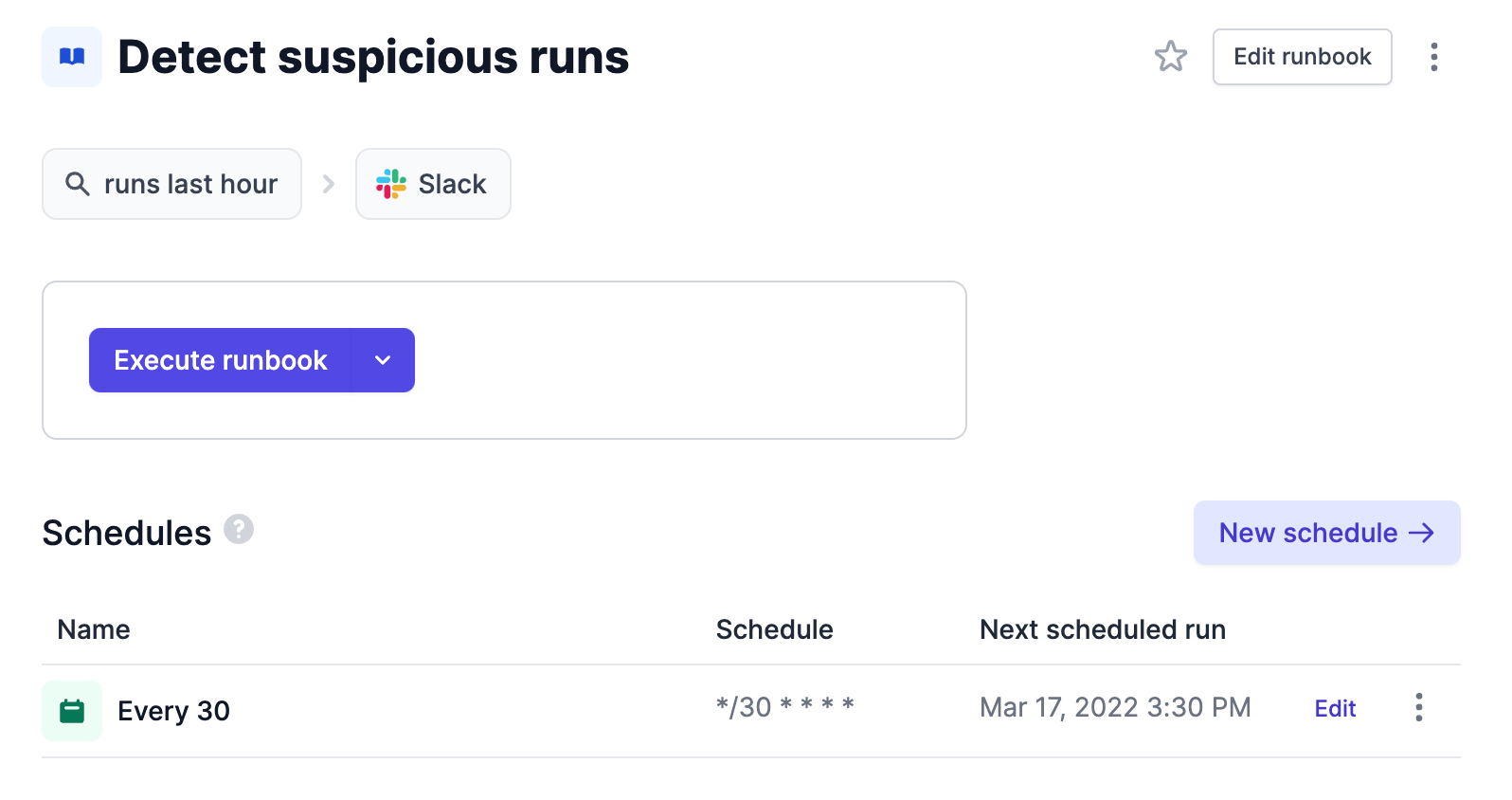
Health checks, monitoring, and reporting
Customers use Airplane tasks and runbooks to maintain data integrity through health checks. You can use schedules to check for system failures, refresh API tokens, and consistently sync rows across datasets, for example.
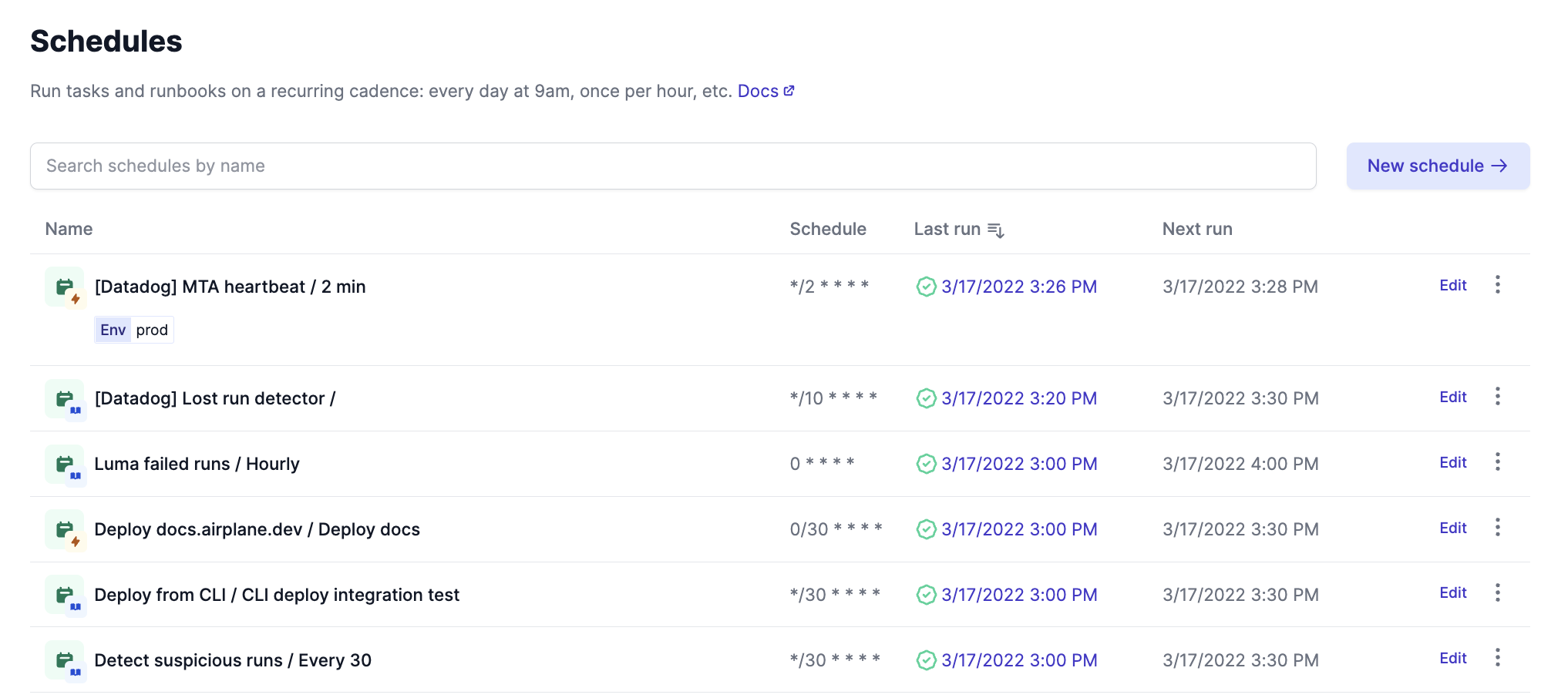
Runbooks can help monitor things like message queues, identify slow or broken queries, and track system performance. You can also autogenerate reports and automatically alert on things such as irregular data patterns, duplicate entries, and missing or flagged transactions.
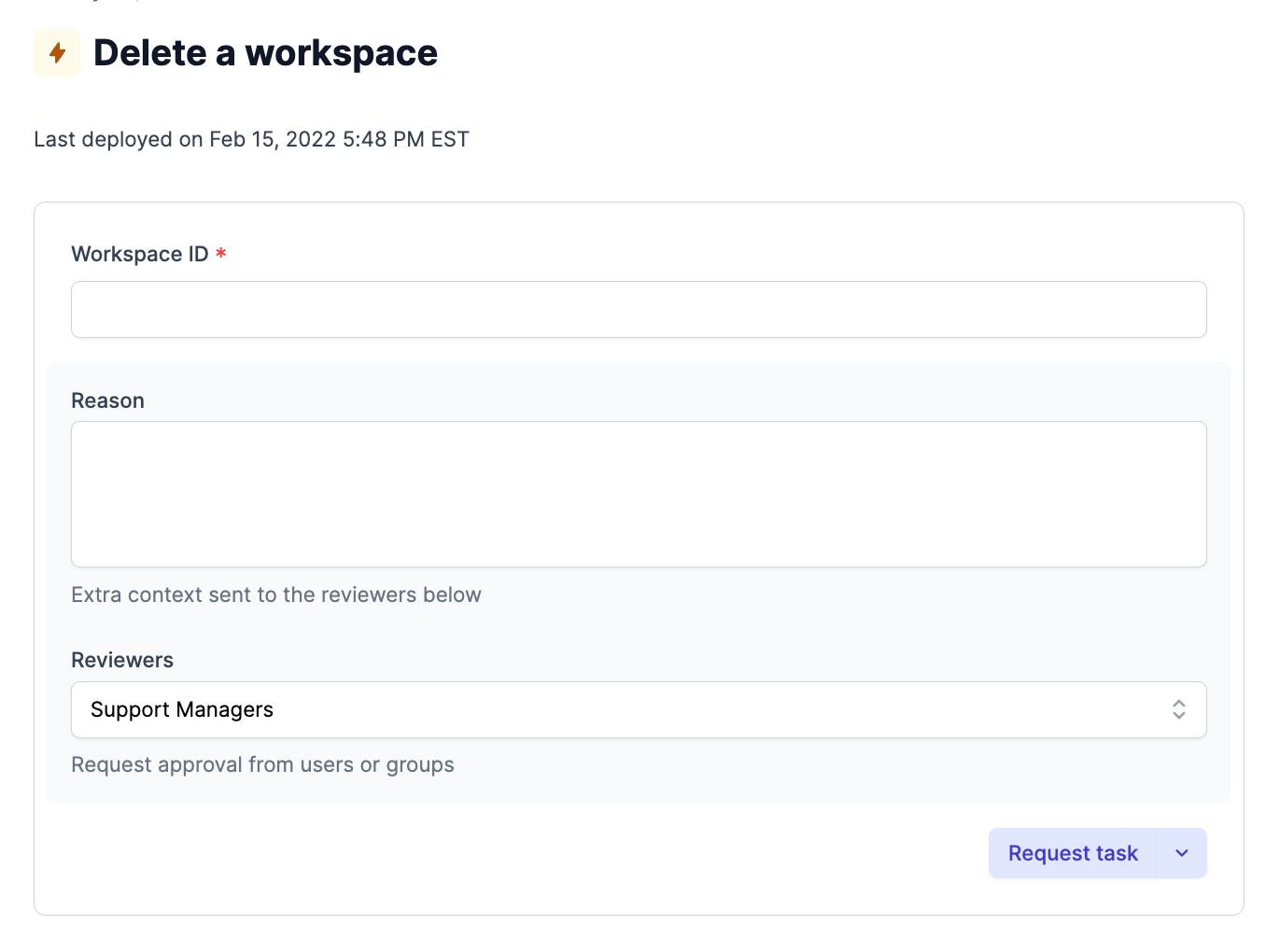
Access controls on sensitive operations
Operations like archiving a workspace, deleting an account, and removing/deleting users tend to be sensitive in nature because they involve deleting data. Rather than wasting time building bespoke approval workflows and micromanaging individual permissions, you can handle these in Airplane using group permissions and approval flows.
Database backups
Use Airplane schedules to automatically run backup jobs at regular cadences.
Debugging issues
Airplane gives you the ability to debug information from prod without giving everyone direct access to the database. For example, you can safely look up object metadata related to an issue you're trying to diagnose and debug. Having constrained, parameterized tasks in Airplane is much safer than giving general DB read access to everyone on the team. With Airplane, users can read from the prod DB, diagnose the issue, and then request the appropriate write action using approval flows in Airplane.